Asymmetric Encryption Algorithms
I
remember a security
administrator
who told me he couldn’t enable encryption in a site to site VPN
because the
firewalls
couldn’t
encrypt high throughput traffic. He said the firewalls didn’t have
enough CPU for VPN data encryption. Obviously, those firewalls
weren’t well sized for his requirements. Encryption
needs powerful
CPU
and/or powerful
cryptographic
cards but it also requires to choose the right cipher suites. Maybe,
this security administrator didn’t have a good firewall to encrypt
the site to site VPN but, maybe, he didn’t know either there are
several encryption
algorithms,
and
if they are configured properly, you will be able to get what you
want.
I
learnt at
University how
public-key cryptosystems work. It’s
easy to understand. There are two keys. A public key and a private
key. The public key is well-known for everyone. It’s like an open
padlock. However, the private key is only known by the owner. It’s
like the key to open the padlock. Therefore, when someone wants to
send something encrypted into the padlock, only the owner can open
the padlock and read the message. Rivest–Shamir–Adleman
(RSA)
is one of the first public-key cryptographic system and it’s the
most used for data transmission.
 |
| Public Key Encryption |
There
is an alternative to the RSA. It’s the Digital
Signature Algorithm (DSA).
This
algorithm was developed by the U.S government and it has the same
security degree as RSA. However, it employs different mathematical
algorithms for signing and encryption. DSA is also an asymmetric
encryption scheme, like RSA, and
it’s faster for signing but
slower for verifying. Therefore, DSA is not a good choice if there is
performance
issues on the client side.
Diffie-Hellman
is another algorithm I've learned, but this one, while I've been
working with Virtual
Private Networks (VPN).
It’s
an asymmetric algorithm useful
to determine a
secret
key between peers. Firstly,
peers agree to use a key, which could be listen by an attacker.
Secondly, they use a private secret key, which is only known by each
of them. Finally, these
two keys are used to get a new one, which is the final key for the
encryption process.
This
final key is, computationally speaking, difficult to get by an
attacker.
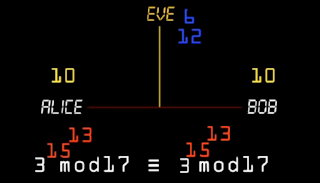 |
| Diffie-Hellman Key Exchange |
These
three algorithms are well-known by most security engineers. However,
Elliptic Curve
Cryptography (ECC)
or Elliptic
Curve Digital Signature Algorithm (ECDSA)
is increasingly used because ECC cryptography provides much strong
security than RSA or DSA with smaller keys. Therefore,
ECC cryptography is the best option for mobile devices due to the
fact that it requires less computational overhead.
 |
| Elliptic Curve Digital Signature Algorithm |
On
the whole, when you are going to configure encryption for whatever,
it’s better to know what algorithm fits with your architecture
because if
you don’t choose the right one, the network
performance
could be degraded.
Regards
my friends. Have a nice day!










Commentaires
Enregistrer un commentaire