AWS Security Best Practices
Hosting
our services into a Cloud Service Provider (CSP),
such as Amazon, is not an easy task when we are thinking about
responsibility. This is because the
responsibility is shared between the Service Provider and our
company. This responsibility could be unclear sometimes. Therefore,
IT engineers have to read and study about how the CSP works to know
what are their responsibilities and what are ours. For
instance, it’s important to know who
is responsible for access management, network traffic protection and
data encryption.
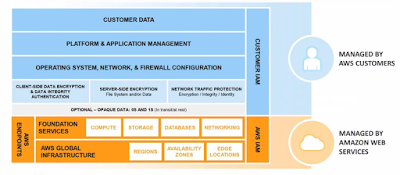 |
| Shared Security Model - Infrastructure Services |
With
regard to Access Management, Amazon has a
service called AWS Identity and Access
Management (IAM) which is useful to
grant access to individual users and manage their credentials. This
is a service where we can apply security best practices like
rotating security credentials
regularly,
defining a strong
password policy and managing
permissions by group or users. In addition, AWS
IAM are able to enable Multi-Factor
Authentication (MFA) for privileged users as well as sending logs to
AWS CloudTrail
for visibility of user activities.
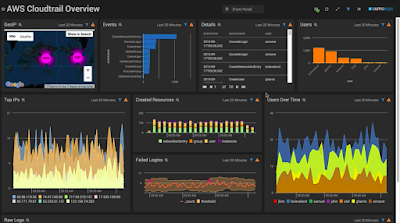 |
| AWS CloudTrail Overview using Sumo Logic |
Creating
our
virtual Data Center has some risks,
if we don’t
configure properly, because we have to
define virtual networks into Amazon VPC
where it’s recommended at least 2 subnets in different Availability
Zones (AZs)
for each layer of our
network. What’s more, we can configure
NACLs with rules similar to our security groups in order to add an
additional layer of security to our VPC. VPC
Flow Logs is another
interesting feature which should be
enabled if we want visibility
of network traffic flows.
 |
| VPC with Public and Private Subnets and AWS Managed VPN Access |
EC2
instances are going to communicate each other but there should be
communication for only those TCP/UDP ports required. Therefore, it’s
recommended to configure
Security Groups
as virtual firewalls to allow and deny traffic to
or from instances.
This is the best way to protect instances,
or group of instances, because instances
which are in a
group are not going to communicate to instances of another group
unless we allow it explicitly. As you can
see, it’s no longer enough a network perimeter firewall to allow
and deny traffic between networks but we are increasingly demanding
firewalls to
protect virtual machines from
virtual machines even when they are in the
same subnet.
 |
| Amazon Security Groups |
When
we are talking about Encryption and Key Management, we have to know
what architecture suits into our organization. There are mainly two
types of architectures into AWS. The
Client-Side Encryption architecture,
where we encrypt our data and manage our
own keys, and the Server-Side Encryption
(SSE)
architecture, where AWS encrypts data and manages the keys for us. We
can use AWS Key Management Service (KMS)
as well as AWS CloudHSM
which help us to provision and use encryption keys to protect our
data. For instance, Netflix
Key Management is done with AWS CloudHSM.
 |
| AWS Services Integration with AWS Key Management Service |
Although
we are moving to the Cloud, security is still a concern by most
companies and we have to configure security measures into our
services to make them safe thus don’t
give up because there are still a lot of work to do.
Do
you want to share with us your Cloud Security Best Practices?









Commentaires
Enregistrer un commentaire