Web Application Firewall - WAF
One year
ago, I was working with Web Application Firewalls (WAF) to protect
web servers against Web
Application Vulnerabilities like SQL injection attacks, XSS
attacks, CSRF attacks, etc with the aim of protecting XML
and Web Services as well as WebSockets.
This kind of firewall is much more than a network firewall because
while an IDS is able to detect and warn attacks, an IPS is able to
detect, warn and block attacks, a WAF is able to detect, warn and
block sophisticated attacks like parameter tampering, hidden field
manipulation, forceful browsing, etc. Therefore, WAF works much
better at the application layer than a traditional firewall.
I’m
going to write about how to configure a basic security policy to
protect web servers, which is something I have taught in the Security
courses on Networks and Systems. First of all, we have to
understand how a common web attack works like SQLi attack, which can
be used to steal databases or bypass login pages. For instance, we
can see the next SQL sentence used to authenticate users in a web
page.
<php
$query =
"select id from users where nick='$username'
and password='".md5($MD5_PREFIX.$password)."'
and suspended=0";
However,
this PHP code has security weaknesses because if we insert the
characters ‘ or 1=1 # into the
login form, we are going to bypass the authentication in the web
page.
<php
$query =
"select id from users where nick='‘
or 1=1 # ' and
password='".md5($MD5_PREFIX.$password)."'
and suspended=0";
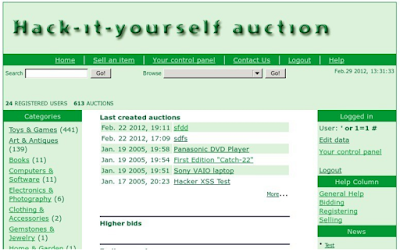 |
| SQLi attack |
Now, it’s
time to protect the web server with a WAF. I’m going to use F5
BIG-IP ASM but there are other manufactures like Imperva, Akamai or
Citrix.
 |
| WAF Architecture |
We have to
create a security policy manually, which builds a basic security
policy in Transparent mode that we can review and fine-tune. In
addition, we have to select the Rapid Deployment (RDP) template to
minimize or eliminate the amount of false positives and the
complexity and duration of the initial evaluation deployment period.
 |
| Rapid Deployment security policy |
After the
security policy is deployed and applied, we can attack the web page
to see attacks detected into the Traffic Learning.
 |
| SQLi attack detected into Traffic Learning |
Once there
are no false positives, we are ready to configure the security policy
into the blocking state and disable the signature staging to actually
block real attacks.
 |
| Learning and Blocking Settings |
If we
attack the web page again, we are going to see illegal requests into
the application event logs as well as traffic attacks will be blocked
by WAF.
 |
| SQLi attack detected into Application Event Logs |
Regards
my friends, protect your web servers and
keep studying!!









Commentaires
Enregistrer un commentaire