Just another cyberattack
Today,
I was thinking to write about errors, overruns, collisions, etc that
we could have in network interfaces which are a mess for network
engineers and, most times, these issues are difficult to resolve
without a good troubleshooting process. However, this
weekend has been a little bit interesting because we have seen how
big companies like Telefonica, and many
others, has
been hit by Ransomware and it has been published to the media.
Therefore, I must write about this issue.
First, I
think it has been another spam and malware campaign, just another,
but this time, many Spanish companies have been affected, which some
of them are from the stock market IBEX35, and this has been the
reason why the media has been speaking about cyberattacks. However,
it's a pity that big companies like Telefonica hadn't applied the
patch on time. Maybe, they didn't have enough time to test the patch
MS17-010
published by Microsoft and they would rather take the risk to be
infected. Unfortunately, this time, their internal desktops were
compromised.
We are
always speaking that small companies doesn't have enough resources to
fight against cyberattacks but we can also see that big companies,
with lots of resources, have the same issues but on a large scale.
Meantime,
we have seen how shares were without any lost, which means investors
don't mind this kind of news.
 |
| Telefonica shares |
There are
many Microsoft products affected in these cyberattacks like IE10,
IE11, Edge, Microsoft .NET Framework, Adobe Flash Player, etc, etc
and most of them are installed by default in most of the Microsoft
Windows Operating Systems.
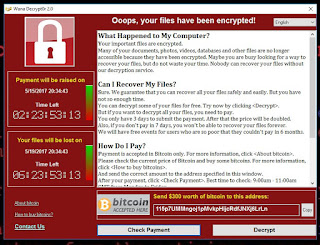
Due to the
high risk of these vulnerabilities, if you don't want to be infected
by HydraCrypter, which is a variant of WannaCry, you should applied
next measures to your organization:
- Limit the user connection to Internet and mail while your are applying patches and upgrading systems.
- Upgrade signatures of your security systems like AntiSpam, IDS/IPS and Antivirus.
- Apply security policies to Internet access with IPS and Antivirus profiles.
- Install security monitoring sensors to analyse traffic on the wild.
- Apply patches to fix the bugs published by Microsoft to desktops and servers.
- Make sure you have backups.
More
specific recommendations could be:
- We can disable file execution with .WNCRY extension by GPO.
- Isolate UDP 137/138 and TCP 139/445 communication inside the network.
- Disable macros and scripts to mail received. We can use Office Viewer instead of Microsoft Office to open attachments.
If we have
done the homework, we shouldn't be worried about this Ransomware
anymore. Why? Because most security systems have already published
signatures to block and detect this malware like, for instance,
Fortinet
or OTX
from Alienvault.
 |
| WannaCry Indicators from OTX |
Many
people are wondering about why last Friday was the day when these
vulnerabilities were exploited massively. Maybe, because last Friday
was when WikiLeaks
published “After Midnight” and “Assasin”, two CIA malware
frameworks for the Microsoft platform and, maybe, the
attackers have taken advantages of these frameworks to develop this
new malware.
 |
| Two CIA malware frameworks |
Regards
my friends, pay
attention, protect your assets and keep calm!!
More
info:










Commentaires
Enregistrer un commentaire