F5 WAF - Elevated Protection
I
wrote about F5
WAF – Good Protection
last week where I wrote down the main security features recommended
for a good protection. These
features, Attacks Signatures, Transparent enforcement mode, IP
Intelligence, Geolocation, Protocol Compliance, Protection from
evasion techniques, Protection from parameter exploits and Threat
Campaigns, are easy to configure and maintain with a minimal
administrative effort and time. However, web
servers can be protected better with elevated protection security
features, which we are going to see below.
Bot
Protection
is a elevated security feature which is able to identify and
classify benign
and malicious bots. The BIG-IP ASM system has a bot detection engine
that uses a combination of known bot signatures, JavaScript, CAPTCHA,
and rate limiting to block bot traffic. Another
interesting security feature for elevated protection is Web
Scraping Protection,
which is useful for blocking extraction of information from a web
application. L7
DoS Attack
Protection
is also recommended because
DoS
Attacks
are not only volumetric attacks but L7 attacks which can deny your
web services with few packets.
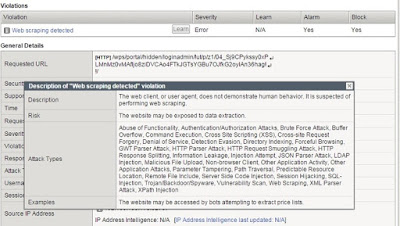 |
| Web Scraping Violation |
Applications
are developed with a language and this language uses a file
extension. Therefore, Disallowed
File
Types
is a best practice where we should configure a blacklist and a
whitelist of file types. This is the best way to reduce the
application attack surface. For
instance, if the web application is developed with .jsp files, other
extensions other than .jsp should be blocked. On the other hand,
External
Logging
is increasingly configured to
send event data to a SIEM
system
for incident analysis and long term log storage. These
systems are able to collect all kind of event data, which are really
useful later on for analysis.
 |
| Allowed File Types |
CSRF
Protection
is also an elevated security feature recommended to block CSRF
vulnerabilities. This
vulnerability exposes users to fraudulent actions such as money
transfers, password changes, and unauthorized product purchases.
As a result, BIG-IP ASM is
able to
apply virtual patching until this vulnerability can be fixed by
developers. Another
security feature interesting for an elevated protection is HTTP
Redirection
Protection.
This
feature will block redirections to another domains which are not
allowed. Therefore,
we can block attackers who want to redirect users to a forged page on
a site that deceptively appears like the one they just left.
 |
| CSRF Protection |
The are
two more security features for an elevated protection. The first one
is Cookie
Tampering
Protection
which is really useful because most applications utilize cookies
to store data. This
cookies have to be protected from manipulations. Consequently, we
should configure a whitelist of “allowed” cookies. The second one
is Behavioral
DDoS
feature which mitigates DDoS
attacks
by analysing traffic behaviour, and using machine learning and data
analysis. BIG-IP
ASM systems monitor application health and apply mitigation
techniques such as slowing down a client, a CAPTCHA request, or
blocking the request.
 |
| DDoS attack summary |
Regards!
Stay at home! Study
at home! Test at home!










Commentaires
Enregistrer un commentaire