AWS Shield & AWS WAF
I’ve
already written about AWS
Key Management Service and AWS
Security Best Practices as well as
how to create
your virtual Data Center into AWS
Cloud with firewalls, load balancers, WAF,
etc. I’ve also
written about Web
Application Vulnerabilities and Web
Application Firewall (WAF).
Therefore, I want to write today about
AWS WAF & AWS Shield, which are useful to protect our
Web
Services and WebSockets.
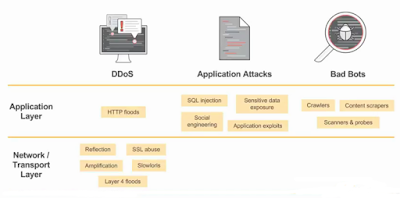
There
are increasingly types of threats. They are increasingly
sophisticated. They are increasingly difficult to detect with
traditional security tools like network layer
firewalls. Instead,
we should deploy and install advanced security tools like SIEM
and WAF
to detect and protect our services
of DDoS
Attacks,
application attacks and bad bots
like HTTP floods attacks, Amplification
DDoS Attacks,
Social
Engineering Attacks,
application exploits, crawlers, Web
Scraping Attacks, etc. Most of them
are advanced attacks difficult to detect by
traditional firewalls.
 |
| Types of Threats |
AWS
Shield is useful if we’re
hosting services
into AWS Cloud and we want DDoS protection without infrastructure
changes. In addition, AWS
Shield also minimizes
impact on application latency and we can customize protections for
our applications as well. There are two
types of AWS Shield into AWS Cloud. The Standard Protection which is
available to all AWS customers at no additional cost for protecting
our services from most common attacks like SYN/UDP floods, reflection
attacks, etc. The Advanced Protection where we pay for additional
protections, features and benefits like protecting against large DDoS
attacks as well as cost protection to absorb DDoS scaling cost.
Therefore, if we want DDoS protection for
our applications,
we should read, study and test AWS Shield
to know which one
suit into our requirements.
 |
| AWS Shield Dashboard |
I’ve
already written about Web
Application Firewalls (WAF), and
AWS WAF is one of them where we can filter web traffic with custom
rules, we can block malicious requests
and we can also monitor
and tune our web applications. AWS WAF is
able to block HTTP floods attacks, SQLi attacks, XSS attacks,
scanners and probes, bots and scrapers, brute force attacks as
well as it’s able to check against IP reputation lists, blacklists
and whitelists. In addition, we can
configure AWS WAF to import rulesets of commercial signatures to
detect general and known exploits.
 |
| Fortinet Managed Rules for AWS WAF - General and Known Exploits |
We
can configure AWS WAF easily and
automatically thanks to AWS
CloudFormation Templates. On
the other hand, If we can
also configure AWS WAF manually. Conditions
like XSS, SQLi or IPs addresses are assigned to rules, then rules are
applied to Web ACLs to protect our web applications.
AWS WAF can protect web applications
deployed with AWS CloudFront
as well as deployed with AWS
ELB. It’s
important to highlight we’ll pay for rules and Web ACLs created
into the AWS WAF.
 |
| Common Attack Protection SQLi Rule for AWS WAF |
It’s
up to you what you need and how much you can afford. AWS
Shield with Advanced Protection along with AWS WAF with Managed Rules
through AWS CloudFront is one of the best security solution but,
maybe, it’s too expensive and too much protection for your web
applications. This is the real cloud, we’ll pay as we go.
Regards
my friends.









Commentaires
Enregistrer un commentaire