This
month is being fearful with the amount of attacks I'm watching
against web applications because attackers have found an easy way to
get into systems taking advantage of the last Apache Struts2
vulnerability with CVE-2017-5638.
Thanks to the Ethical
Hacker course I received two years
ago and my knowledge about XML
and Web Services, I'm going to
highlight some steps to know how to exploit this vulnerability, of
course, to know if our web services are vulnerable, and
we are also going to see what we can do to protect our organization
from this attack.
This
is a critical vulnerability due to an error handling issue when we
send crafted HTTP request to a web server containing a malicious
“Content-Type” or “Content-Disposition”
field. The remote attacker can exploit this to execute arbitrary code
within the context of the application, via a crafted request.
Therefore, systems can be compromised and
remote attackers can gain control of vulnerable systems. Actually,
the affected products are from Struts 2.3.5 to 2.3.31 and from Struts
2.5 to 2.5.10.
How
can we know if our web servers are vulnerable? First, asking to our
developers to know the Struts version they are using for developing
web applications. If we are not lucky, we can check it by our own. Struts 2 is built with Maven,
as a result we can find the pom.xml
file from the source tree or in jars under META-INF
folder:
 |
| Struts version |
Another
way to know if our web applications are vulnerable is with
the Nmap tool which has an script NSE called http-vuln-cve2017-5638
that help us to detect whether the specified URL is vulnerable to the
CVE-2017-5638. As we know, this is a useful tool for
scanning
and enumeration
before attacking.
 |
| Nmap NSE script http-vuln-cve2017-5638 |
 |
| Nmap request and Server response |
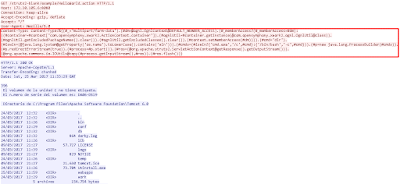
As
you can see, my lab is vulnerable, this is because I have installed a
Windows Server 2012 with
Apache
Tomcat 6 server
+ MySQL
database 5.5
+ Java
JRE environment
+
Struts
2.3.20 Apps.
This
is an easy laboratory to deploy because after installing Apache,
MySQL and Java, we just have to copy the struts2-blank.war file into
the Apache Software Foundation → Tomcat 6.0 → webapps folder and
restart the Tomcat service.
 |
| Struts Hello World Webpage |
Regards my
friend and remember, open you eyes and protect your web servers.

















Commentaires
Enregistrer un commentaire