WebSockets
I'm
not a developer but if we want to protect our web services, we should
understand how they work. This is why I'm reading, learning and
studying about web services lately because I think there should be a
narrow line between a Web Security Engineer and a Network Security
Engineer. Both should speak the same language. Therefore,
this is mandatory when we are installing for example a Web
Application Firewall and we have to choose or configure an XML or JSON
profile for protecting our web services.
HTML5
is a markup language with a lot of improvements regards HTML 4 and
XHTML 1. For instance, we can forget flash
and their upgrades, we have to change the way we know cookies thanks
to the new Web Storage feature in HTML5, better multimedia
interaction, and the new WebSocket feature,
which we are going to write here today.
If
we connect to some web application like those hosted in the
www.websocket.org website, we
can test and capture network traffic to analyse HTTP headers and the
handshake process. In a WebSocket,
we'll see new headers like Upgrade,
Connection, Sec-WebSocket-Key, Sec-WebSocket-Version or
Sec-WebSocket-Accept and others optional headers as well. In
addition, we'll see the WebSocket protocol defines a ws:// and wss://
prefix to indicate a WebSocket and a WebSocket Secure connection,
respectively.
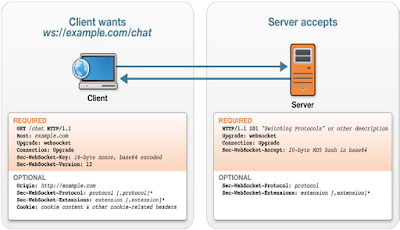 |
| WebSocket Headers |
The
handshake process is a little bit different from what we know with
HTML 4. In a WebSocket, we'll have the Upgrade and Connection headers
with the websocket and Upgrade values, respectively, for establishing
a connection. Moreover, the web server will send a 101 code to the
client for switching protocols. During data
transfer, there will be a two-way and full-duplex communication with
persistent connections between client and server. In the end, client
and server can close the connection and it can be initiated by either
peer.
 |
| WebSocket Handshake |
We
have new protocols, new methods and new standards but threats are
still there. A variation of Cross Site
Scripting Attack (XSS) is the Cross Site WebSockets Scripting Attack
(XSWS) or the Cross Site WebSocket Hijacking Attack
(CSWSH). For
instance, we can find an Online
Cross Site WebSocket Hijacker Tester
from ironwasp.org, which is an
online tool to easily check for CSWSH issues. There are more tools
like a WebSocket Message Analyzer or a WebSocket Client in the
IronWASP application for WebSocket Security Testing.
 |
| Online Cross-Site WebSocket Hijacking Tester |
Internet
is full of pentesting tools to learn about it and getting fun.
Another tool for testing vulnerabilities in WebSockets is the
socket_io_client
developed by Krzysztof Kotowicz, which is a simple malicious
Socket.IO client written in Python.
 |
| Malicious Socket.IO script |
Technology
are evolving increasingly faster and we
have to adapt our appliances, tools and knowledge at the same speed
for protecting our services and our
information.
Regards
my friends, don't forget to keep studying!!









Commentaires
Enregistrer un commentaire